Tags: Sudo Root
Setting up a Graphical Sudo Prompt on X.org
If you've installed a Linux distro that requires a little set-up (or you've
just tinkered around with your system a little) you'll have noticed that
there's a file called /etc/sudoers. And there's probably only a few things
that you're looking at in this file: who can sudo and when.
Gentle Introduction
sudo means "substitute-user do". As such it's pronounced as "suu-dew",
not "suu-dough." It allows one user to execute a command as another user; by
default (i.e. if one simply types sudo <command>) the command will be
executed by root.
The principle of multi-user systems is this: every abstract user on the
computer system ought to be treated as if it were owned and used by only one
human user on that computer. That is to say: when I am logged in as root
(i.e. the super-user who can execute any command) the computer should treat
me as root, not as yumi. Consequently I should act as root would and
not as yumi would. Since computers are very good at following rules, as
long as I pass the criteria to masquerade as a different user this
abstraction is respected.
Instead of using sudo, one may also use su. These achieve the same
effect of masquerading as a another user; the only differences are that
sudo will execute only the passed commands and will prompt for your
password (given that you're allowed to run sudo); meanwhile su will
simply log you in as the other user but will prompt you to enter that user's
password.
Securing your /etc/sudoers file
You may have noticed that there is a line in the /etc/sudoers file which
is as follows:
## Uncomment to allow members of group wheel to execute any command
# %wheel ALL=(ALL) ALL
So if I am in the wheel group, I may execute any command as any user
given that I know my own password. That makes me a little un-easy to
start with (What if someone knows my password? Now they can do anything!)
but if you are the power-user for the machine then this is a little safer
than logging in as root; thus I have found it useful for day-to-day
management and more convenient that logging in as root with that lengthy
password all the time.
However attention must be brought to the next line of the /etc/sudoers
file as well:
## Same thing without a password
# %wheel ALL=(ALL) NOPASSWD: ALL
Well, there is a group of such people who think this is no problem at all. Let me remind you that this actually is a problem: any scripts you execute at all have the potential to ERASE THE ENTIRE SYSTEM NO QUESTIONS ASKED WITHOUT EVEN KNOWING YOUR PASSWORD!!!
Consider: you. You download a script from Github that prints colors onto your terminal using ANSI escape codes. Further consider that this program is over 1000 lines long (it prints very pretty colors) and consequently you have no time to proofread every single line and verify that it genuinely does what you think it should.
If that program was written by a malicious user who intends to execute
sudo su (no matter how deep within the source tree such a command is
buried) and if you use sudo without a password then you've been completely
fucking pwnt; the script which was previously executing as you is now
executing as root and now can accordingly wipe the root partition, steal
passwords, install backdoors and generally raise hell. A clever malicious
user would not go straight for wiping the root partition for lulz but rather
would exploit your kindness / generosity in being so simple-minded and
install a key-logger to silently monitor your system until s/he found you so
boring that it'd be preferable to blow up your hard-drive rather than
steal your credit-card number.
But seriously, this is a breach of security to allow root access without a password.
Active Measures you can take Today to Secure your Friend root
Use the first line recommended above: force users (even if they are in
wheel) to enter a password to sudo; even further (and especially if you
are using a personal computer) I charge you to force logins everytime i.e.
remove the timeout by adding / editing the following line
Defaults timestamp_timeout=0
That way you'll need to enter your password every command. If you need to do
a lot of systems administration work then I recommend logging in as root
by using:
sudo su
That's what the super-user account is for anyway, right?
Graphical Logins
If you'd like to execute a command which requires root persimmons via
key-bindings (in this example using a window-manager for X.Org) then you
will need a graphical prompt which allows you to enter your root password.
Fortunately such a program already exists and is called x11-ssh-askpass.
*-askpass Utilities
The *-askpass utilities are very simple; running the command will spawn the
prompt (not requiring that it be graphical at all; historically these
commands have mostly spawned in their own window) and will echo your input
to stdout after you confirm your entry. They interface with applicable
programs like sudo and ssh via special configurable variables.
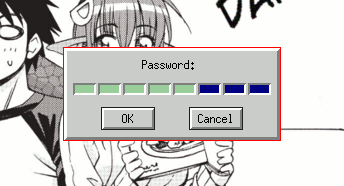
ssh uses the special environment variable SSH_ASKPASS; sudo uses
SUDO_ASKPASS. These variables only need to be a part of the environment
which executes the sudo commands for the graphical prompt to be displayed;
if a display cannot be found, sudo and ssh will default to the typical
text-based input. The *-askpass utilities are widely available in the
repositories of many un/popular flavors of Linux; these types of programs are
so simple that even compiling one from source is hardly a hassle.
Once you've installed a *-askpass program (I recommend
x11-ssh-askpass) then I recommend also putting the following in your
~/.bashrc.
if [[ ! -z $DISPLAY ]]; then
export SSH_ASKPASS="/usr/bin/x11-ssh-askpass"
export SUDO_ASKPASS="/usr/bin/x11-ssh-askpass"
alias sudo='sudo -A'
fi
Because .bashrc is executed by both login and non-login
terminals this will tell terminals which are part of an active X.org
session any sudo or ssh commands run in terminals on X.org will spawn the
password utility. If your window-manager is to execute sudo or ssh commands
on your behalf then also put the above in your ~/.xinitrc without the
enclosing if block.
Benefits
Graphical prompts (esp. full-screen ones) prevent me from careleslly typing
my password into a public chat room if my window becomes unfocused;
additionally one may command the window-manager to execute sudo commands
without problem.
Conclusion
Correctly setting up sudo and optionally its x11-ssh-askpass graphical prompt is
an important step forward to securing your personal computer / home-server;
I hope that you're able to take the knowledge exposed here and apply it to
your personal setup ^.^
- Last Modified
- First Written
Related / Browse
- 25-November
-
I
Sort
November 25, 2018
- Influence
-
Game
World
November 6, 2018
- May-16
-
Something
People
May 16, 2016
- August-06
-
Festival
People
August 6, 2018
- April-14
-
Cannot
Year
April 14, 2016
- Idle Thoughts on Housework: Cooking, Cleaning and Generally Appreciating Oneself
-
Things
Work
January 16, 2019
- Jan-11
-
Music
Do
January 11, 2018